CICS is an online transaction processing system residing between the z/OS IBM mainframe operating system and enterprise applications. Designed to build customer transaction application programs, it can rapidly process large volumes of work. CICS mainframe modernization is often used in financial services for credit card processing and banking transactions.

CICS was introduced in 1968 as a program offering to support BTAM terminals. Featuring assembler macros that supported a limited number of functions, the program was not expected to last more than a few years.
In 1974, CICS/VS 1.0 was brought into play. It introduced management functions and support for DOS/VS, OS/VS1, and OS/VS2 (the latter both used VSAM as a file storage access method). At a macro level only, CICS/VS 1.0 was HLL supported through pre-processor standards.
1986 saw IBM also announce CICS support for the record-orientated file services defined by Distributed Data Management Architecture (DDM). Throughout the 1980s and 90s, CICS continued to run on successive versions of its mainframe operating system - from MVS in 1987 and ESA in 1989 through to VSE in 1995 and OS/390 in 1996, eventually transitioning to z/OS in 2001.
Today, CICS delivers significant capabilities to improve the developer experience, including frameworks, build tools, and various APIs. The latest z/OS iteration provides support for Java 11, Jakarta Enterprise Edition 9.1, and Eclipse MicroProfile 5 and features improved security and compliance management with support for TLS 1.3.
Through the iterations of z/OS, CICS remains the main z/OS transaction processing middleware.
With OpenLegacy, you can generate new digital solutions from your legacy IBM mainframe CICS system automatically, easily, and quickly. This is especially important in a world where companies are grappling with modernization, migration, and transformation.
By connecting legacy systems directly to the modern world with standard microservices-based APIs, OpenLegacy bypasses complex ESB and SOA layers.
Major global enterprises depend upon CICS applications to effectively manage high-volume transactional processing requirements. The challenge is in fully realizing your digital transformation while making the most of the powerful system you’ve already invested in.
OpenLegacy has built an approach that helps companies like yours deliver in-demand modern digital services with no complexity, no middleware, and seamless access to a modernize-in-place approach.
Modern digital services are a key way for users to efficiently access accounts and systems. They allow the company to integrate with digital services like FinTech (financial technology) and InsurTech (insurance technology).
These types of digital services give companies the ability to extend their systems to partners, customers, and others who need secure, simple access.
Open your system up to a world of possibilities for partners, customers, and stakeholders. With OpenLegacy, you can leverage your existing IBM CICS investment and accelerate virtually any type of innovation.
We automate the process and create complete integrations in days or weeks, versus the months it takes for other solutions. The user picks exactly what to expose, how, and to what, and the rest of the process is automated.
Forget the ways you used to connect with CICS. OpenLegacy’s platform parses the core assets and its adapter simplifies what needs to be done. Then, its platform automatically generates interfaces that connect to the CICS adapter.
All you have to install on your CICS system is our adapter, which is a simple CICS program. The OpenLegacy adapter doesn’t require any additional resources or facades. Generate your digital assets as cloud-native microservice-based APIs or nodeJS functions.
OpenLegacy’s development process uses industry-best practices related to data security. These include but are not limited to:
Serving pages over HTTPS (including the HTTP Strict Transport Security Header), secured cookies, and Public Keys.
Check out our many detailed case studies spanning multiple industries. Many of ourclients are large, global corporations that we cannot mention by name. However, reference calls can be arranged.
*TLS version is set by CICS or AT-TLS

“OpenLegacy helps us set the mainframe free, finally. Instead of being a prohibitive factor for new projects, it’s now the enabler – with OpenLegacy generated APIs that connect to any other system in our environment.”
Our open standards approach has enabled us to help a wide range of organizations address their unique business logic challenges, while maintaining their existing CICS investment. OpenLegacy has helped clients to:

For a credit card company an IVR system is a key component. They needed to replace their IVR system but system integrators quoted 3 developers for 2.5 years. This was too long and expensive. with OpenLegacy it took 1 developer, 6 months.
Before OpenLegacy CitiBanamex could not dream of connecting with external systems through OpenBanking APIs. Now this is easy and fast.
OpenLegacy's architecture does not involve any middle layers such as ESBs and MQ. Due to removing this layer we now have stunning performance improvements.
Bank Hapoalim implemented an API factory using core assets which now produces APIs on a fast cadence (5 every 2 weeks with 1 developer). This speed alllows them to perform a complete interface changeover across the entire organization.
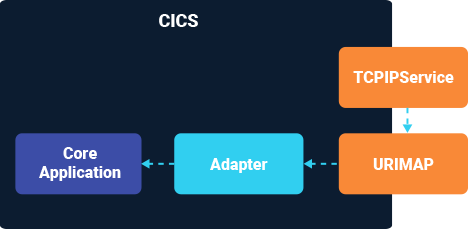
The overall process flow is:
The details of the CICS system and how it works with multiple TORs and AORs are thus:
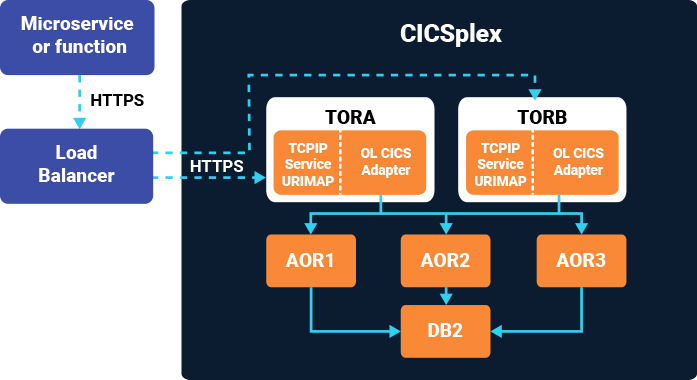
CICS Transaction server V4.1 and above with TCPIP enabled on the CICS SIT.
COBOL programs cannot recognize CICS commands, as these are coded within EXEC CICS and END–EXEC scope. To run a CICS-COBOL program, you must first pass this to the CICS Translator.
The translator will convert all the CICS commands to COBOL call statements, and this modified source can then be handed to the COBOL compiler. An integrated CICS translator is required to use the latest features of this.
For DB2 commands, the sequence of preparing load modules looks like this: DB2 Pre-compiler, CICS Translator, COBOL Compiler, and Link Editor.
In the first instance, you should work with precompilation. If the translation is completed as the first task, CICS Translation will try to recognize DB2 statements and issue diagnostic messages.
So, if you handle precompilation initially, all DB2 statements are converted into COBOL call statements in the first phase, lessening the translation time.
CICS provides services to enterprises to alleviate their security concerns and handle transactionality—or the exchange of data between new and existing online applications. A CICS transaction is typically interactive and is a set of operations that performs tasks together.
Used across communications, hospitality, banking, airlines, and Fortune 500 companies, CICS specializes in reliably processing large quantities of real-time, online transactions and transaction management. It can support thousands of these per second, which is why it’s commonplace in enterprise computing.
Some typical examples of CICS transactions include:
These transactions create large datasets, which require either permanent or temporary storage. It’s imperative to keep them safe as they often contain important (and sometimes sensitive) business and customer information.
It’s possible to write Java application programs that use CICS resources but can interact with other programming languages too. This makes it so programmers can facilitate transactions in dozens of areas and for innumerable purposes.